1Password is the easiest way to store and use strong passwords. Log in to sites and fill forms securely with a single click. 1Password is just one of many different password managers, and plenty of its competitors are high-quality as well. Still, after a few rounds of Tech.co's rigorous testing, we've determined that.
Is it possible to have one password for everything? That is, one password to gain access to systems, applications, files, networks—virtually any IT resource? With so much complexity in the modern identity and access management (IAM) space, it’s easy to understand why this question is on the minds of so many IT admins and MSPs. Fortunately, it is possible to have one password for everything. But before we explain how, let’s analyze why having one password is so difficult to achieve in the first place.
A History of Password Management
Copy to clipboard word for mac. 1Password is a password manager that keeps you safe online. You want to use different passwords for every website, but it can be hard to keep track of them all. With 1Password you only ever need to memorizeone password. All your other passwords and important information are protected behind the one password only you know. 1Password manages everything for you: generating, saving, and filling your passwords.
Windows® Password Management
In the beginning, there was one password. Users only needed one password to gain access to virtually all of their IT resources. It was a time when legacy identity management solutions like Microsoft®Active Directory® (AD) were new to the market, and IT networks were predominantly on-prem and Windows-based.
One Password Software
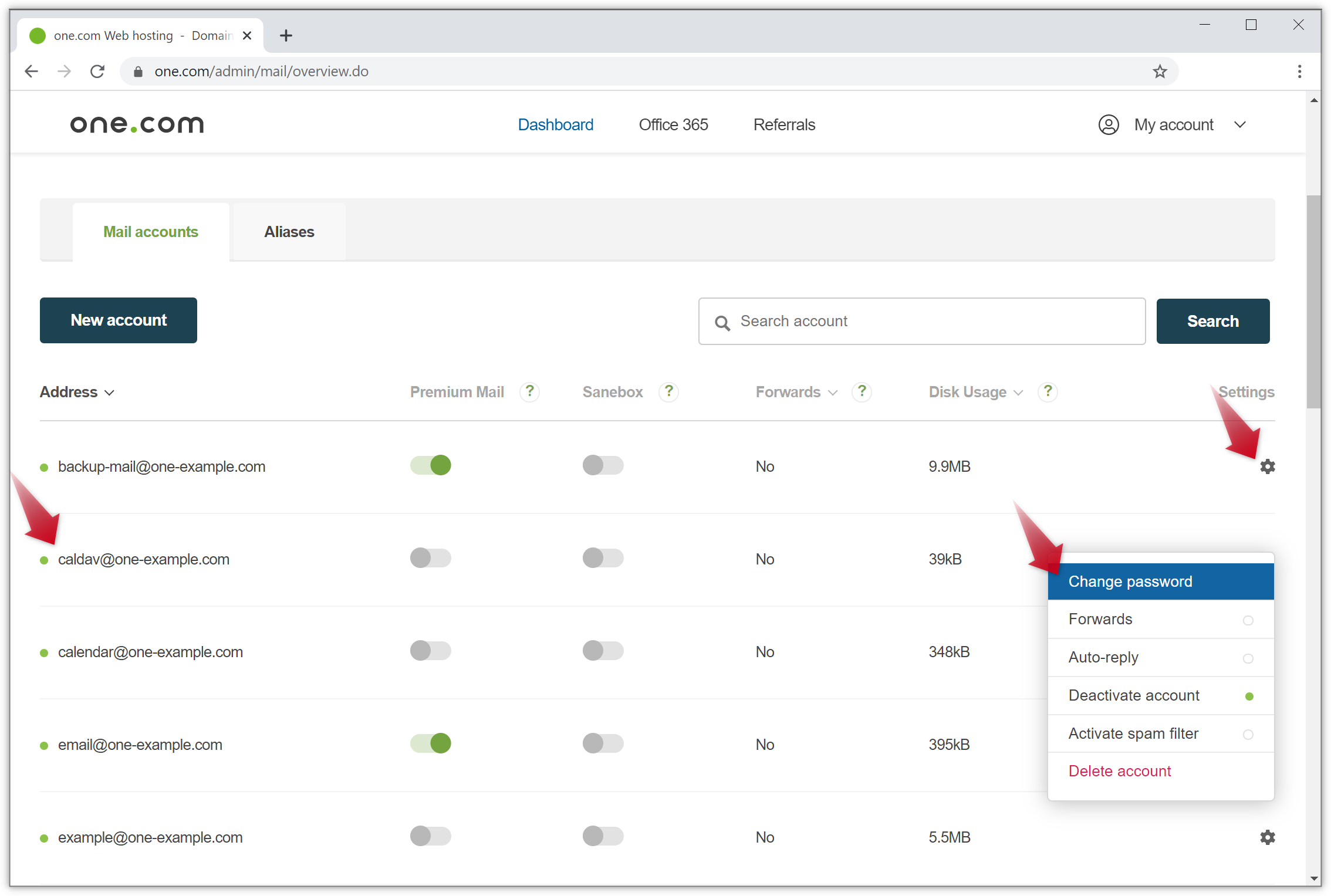
The Windows-centric nature of traditional networks enabled IT organizations to leverage AD to securely manage and connect their users to all of the Windows-based resources they needed for work, including systems, applications, files, and networks. In turn, users only needed one password to gain access to it all, and password management was relatively straightforward for IT admins. They could manage passwords throughout their organization from one centralized location.

Decentralized Password Management
Then, new innovations such as web applications, cloud infrastructure, virtual file storage, and remote networks came to market. The majority of these new innovations were not on-prem, nor were they based on the Windows OS. Consequently, IT admins were unable to leverage AD to manage them directly, often having to manage new innovations independently, or not at all. In either case, the downstream effect was that users then required multiple passwords, one for each of these new innovations.
Converting photo is sketch for mac. Having multiple passwords presented a number of challenges for users and IT admins. For one, users had to memorize individual passwords for each resource, which often resulted in people creating weak passwords (e.g., Password123) shared across multiple resources. Two, IT admins were unable to manage user credentials with any efficiency, thus preventing them from properly enforcing password complexity policies at scale and saving users from their own bad habits. Three, the combination of weak passwords and a lack of centralized password management exposed numerous security vulnerabilities, to which bad actors were quick to exploit.
One Password App
SSO, PIM, Directory Extensions, and 2FA
In response to these critical issues, a number of vendors piled into the IAM space to help manage user credentials. They offered add-on solutions which could be layered on top of AD, such as web application single sign-on (SSO), privileged identity management (PIM), directory extensions for macOS® and Linux®, two-factor authentication (2FA), and many more—all of which were designed to extend AD credentials to previously unsupported IT resources. Yet, while the add-on approach once again enabled users with one password for everything, it came at the expense of significantly added costs, complexity, and management overhead for IT admins. In other words, IT organizations were forced to choose the lesser of two evils.
To add fuel to the fire, the rate of new innovations coming to market has increased exponentially, especially after the rise of cloud computing. And, while vendors in the IAM space have done their best to keep up with the pace of these new innovations, IT organizations simply could not patch their legacy IdP indefinitely. Not only is the infrastructure required to support such a complex network cost-prohibitive, especially for smaller organizations and startups, but it is also difficult to manage effectively. In fact, these challenges have forced many smaller organizations to revert back to managing their IT resources independently, yet again requiring users and IT admins to juggle multiple passwords. So the question becomes, is it possible to have one password for everything, without the hassle of having to maintain a costly on-prem infrastructure?
One Password for Everything, Done Right
Quest One Password Manager
Fortunately, this story has a happy ending. It comes in the form of the JumpCloud® Directory-as-a-Service® platform, which is basically AD reimagined for the modern era. Essentially, the Directory-as-a-Service platform shifts the concept of the core IdP to the cloud. Thus, eliminating the need to maintain a complicated identity management infrastructure on-prem.
Further, the JumpCloud platform leverages secure and open protocols such as LDAP, SAML, RADIUS, SSH, and REST among others. These protocols work in harmony with the JumpCloud System Agent to connect users to virtually any IT resource, rather than trapping IT organizations into a gilded cage of proprietary resources. In doing so, IT admins are free to choose the best IT resources for their organization, knowing they can effectively manage the complexity of modern networks from one centralized location, and provide their users with one password for everything via the JumpCloud Directory-as-a-Service platform.
Sign up for a free account Mbox mini 2 driver mac download. to see the future of identity management in action today. Your first 10 users are free forever. Contact JumpCloud to see how the Directory-as-a-Service platform can provide one password for everything, without anything on-prem and without the help of third-party tools. You can also browse our Knowledge Base or check out our YouTube page for supplemental information, and don’t hesitate to reach out to our success team if you have any questions.
